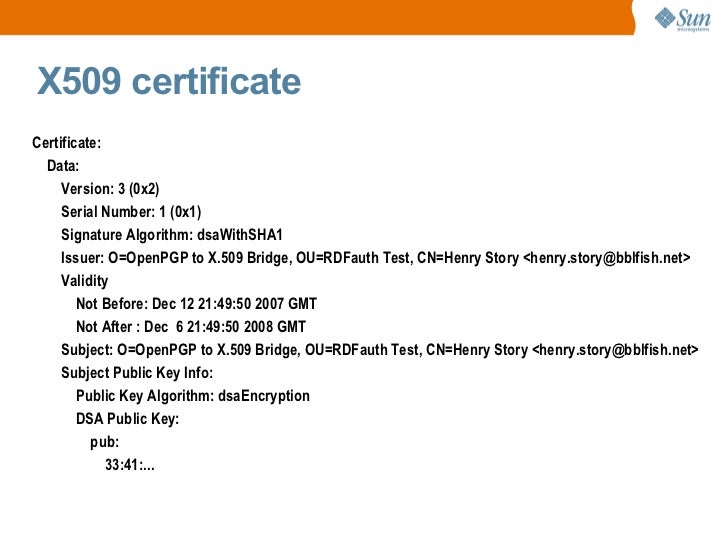
Each certificate is required to have a serial number. This serial is assigned by the CA at the time of signing. Because the data type is specified as a non-negative integer of up to 20 octets length (160 bit), a CA can create a astronomical high number of certs.
- Kumpulan Serial Number Idm
- Pta Certificate Serial Number
- X509 Serial Number Max Length
- Python X509 Serial Number
- X509_get_serial_number
Join GitHub today
GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software together.
Sign upKumpulan Serial Number Idm
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Comments
commented Sep 21, 2015
I think I already know the answer to this, but I'll put it out here for comment. There is an issue, golang/go#8265 that references this section of the x509 code. The certificates generated by vCenter (non-appliance versions) seem to have the negative serials referenced in the issue. Some folks have worked around this by applying fix (see zmap/zgrab@a3d044e), but I was curious as to if this project intends to apply a workaround (or option of one). |
Pta Certificate Serial Number
commented Sep 22, 2015
I was unaware of this issue. Where/how did you generate these certificates? If it is possible to generate new ones that don't have this issue that clearly is preferable over importing the standard library's x509 and subsequently ssl/http packages... |
referenced this issue Sep 29, 2015
OpenError setting up client #30
X509 Serial Number Max Length
commented Sep 30, 2015

I'm also seeing this issue on a Self Signed cert from vSphere. I have no control to generate a new one: Error: Post https://ldnwvvcent01/sdk: tls: failed to parse certificate from server: x509: negative serial number Going to attempt the fix, just replying for visibility. |
Python X509 Serial Number
commented Oct 16, 2015
Hello, For those that need a workaround. We simply configured an apache proxy in front of vSphere to handle this problem. It's all working now. |
commented Nov 13, 2015
I also wanted to leave a comment here, since this 'issue' is not resolved yet. We are working on a large set of x509 certificates and found approximately 100000 certificates with a negative serial number -- all of them which can't be processed due to this issue. Quoting RFC5280, again: 'Certificate users SHOULD be prepared to gracefully handle (...) certificates (with a negative serial number)' So, when we become prepared? As far as I understand the other comments this is not a technical problem, but rather a conflict of opinions? |
commented Nov 17, 2015
@duesee We're really at mercy of the standard library here. I don't want us to maintain a copy of the x509 package just to fix this issue. Could you leave a comment in golang/go#8265 to confirm you're seeing this issue as well? Looks like they're looking for more instances of this problem before fixing it. |
referenced this issue Nov 18, 2015
Closedcrypto/x509: unable to parse certificate with a negative serial number #8265
commented Dec 1, 2015
This was merged and is lined up for release in Go 1.6. Good news :) Closing this issue. |
commented Dec 2, 2015
Good news! Thanks |
commented Feb 26, 2016
Will there be a new release packaged using Go 1.6? |
referenced this issue Feb 26, 2016
Closedgovc complains about certificate even with GOVC_INSECURE=1 #451
commented Feb 27, 2016
Released v0.4.0 built with go 1.6: https://github.com/vmware/govmomi/releases/tag/v0.4.0 |